A systematic review on security in Process-Aware Information Systems – Constitution, challenges, and future directions - ScienceDirect

Access Control: Don't Give Cybercriminals the Keys to your Business | 2020-03-05 | Security Magazine

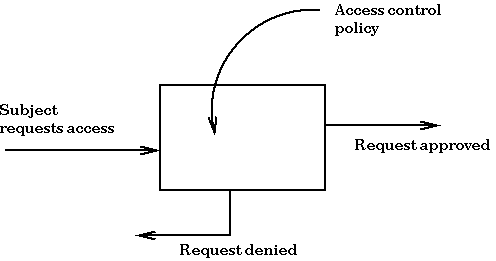
Free Online Course: Information Security - Authentication and Access Control from edX | Class Central

An example of interdependencies between access control and other topics... | Download Scientific Diagram