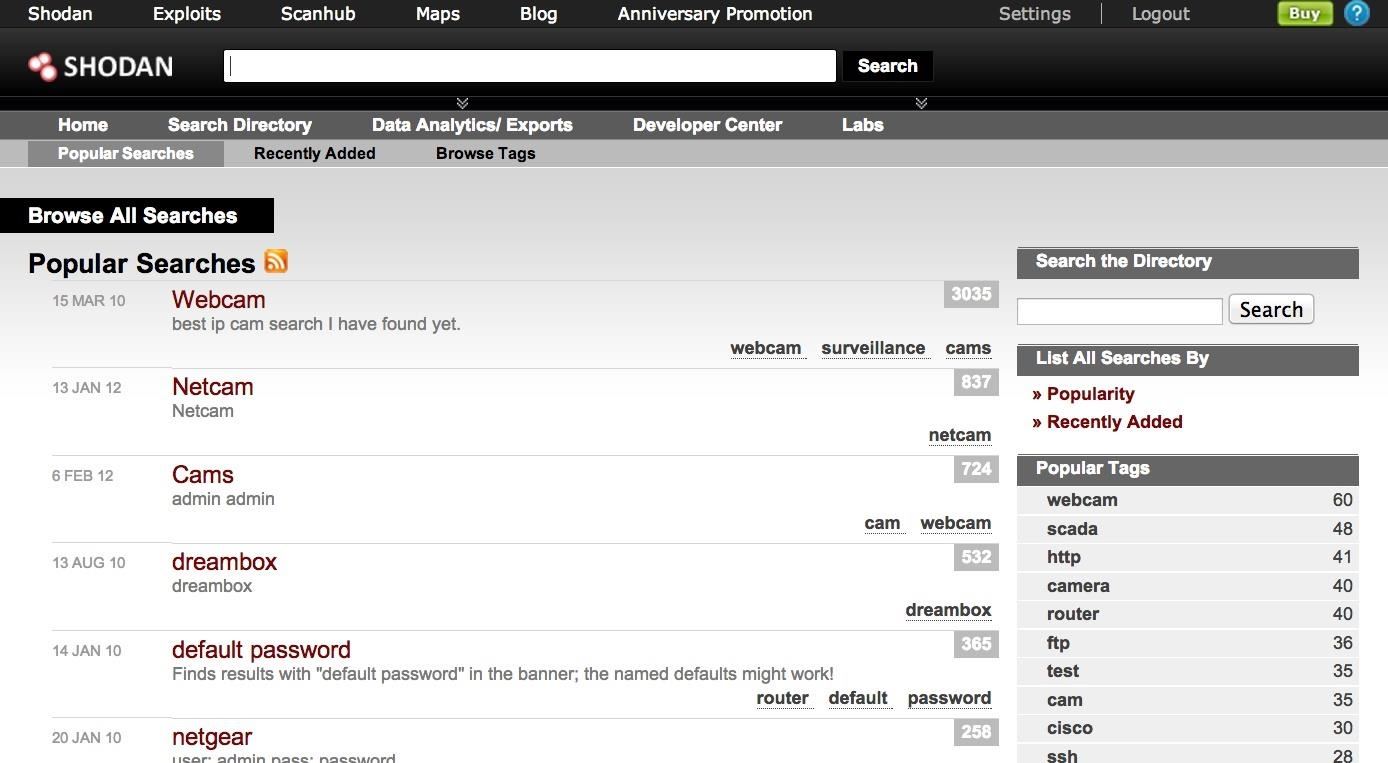
Hack Like a Pro: How to Find Vulnerable Targets Using Shodan—The World's Most Dangerous Search Engine « Null Byte :: WonderHowTo
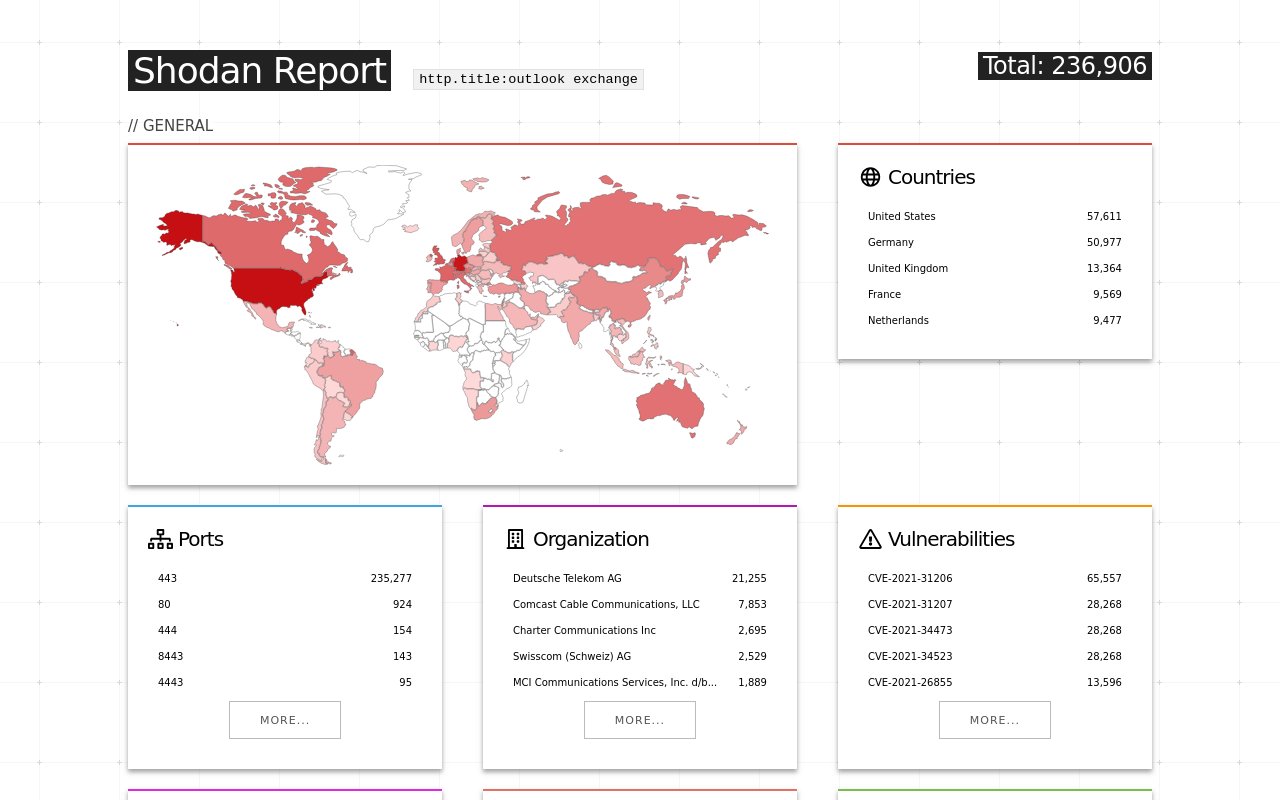
Shodan on Twitter: "More than 18% of Exchange servers remain unpatched for the ProxyShell vulnerability. Nearly 40% are vulnerable to CVE-2021-31206: https://t.co/7yetz9GoJw https://t.co/0r2AOQsibB" / Twitter
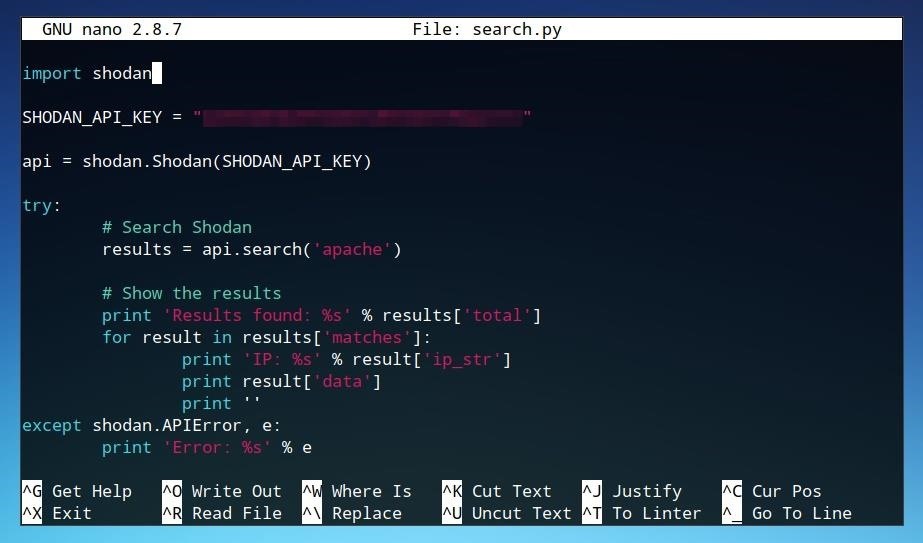
The Hacks of Mr. Robot: How to Use the Shodan API with Python to Automate Scans for Vulnerable Devices « Null Byte :: WonderHowTo





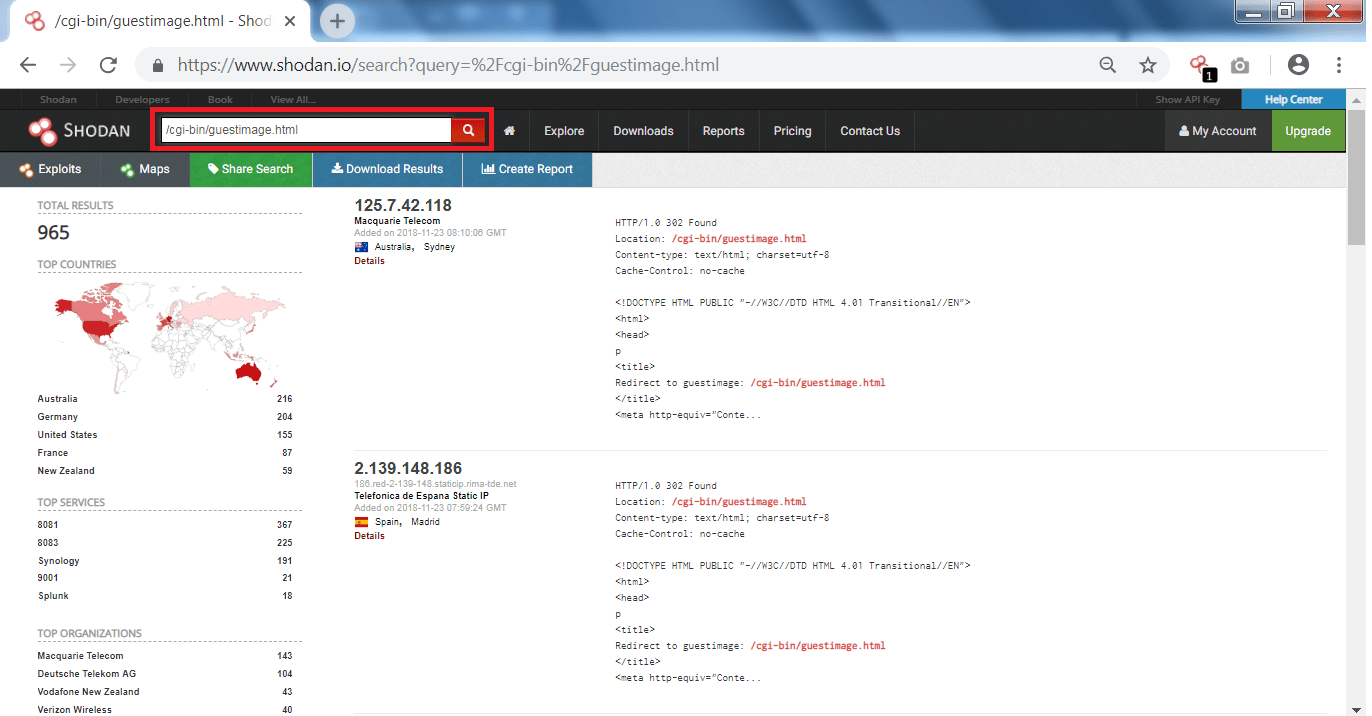

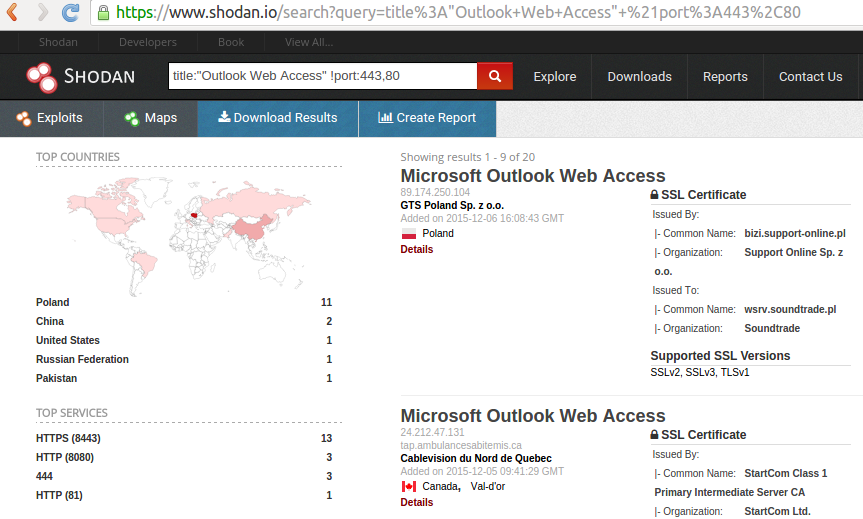
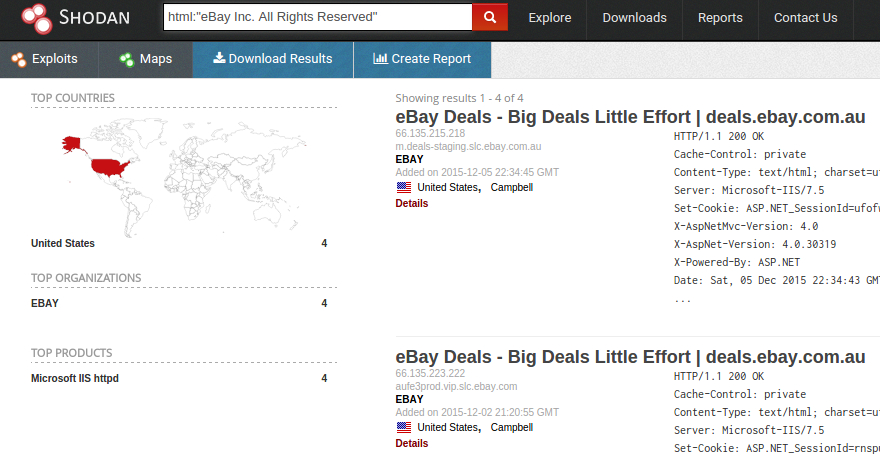


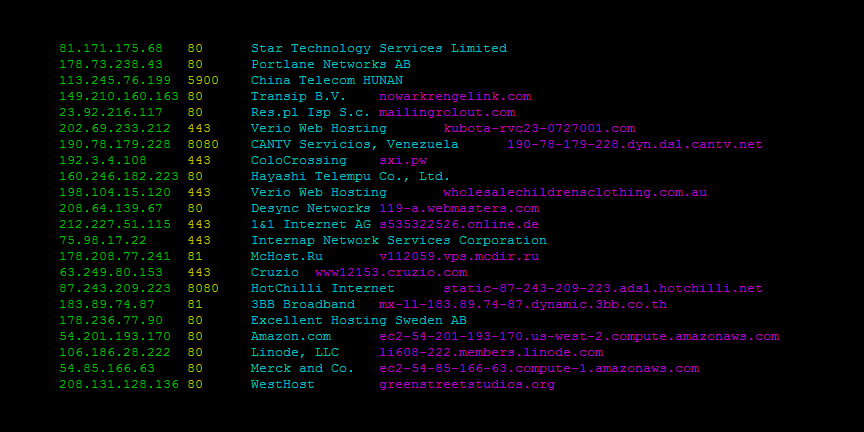

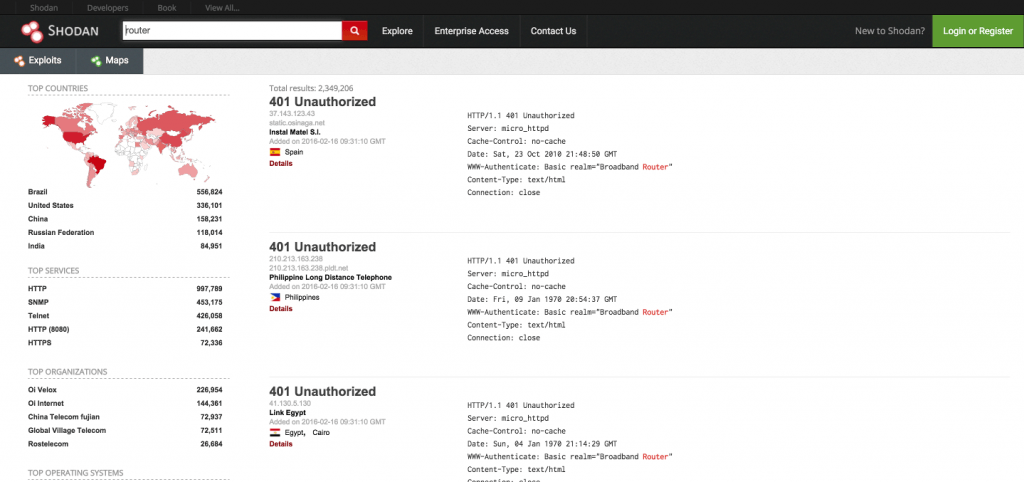

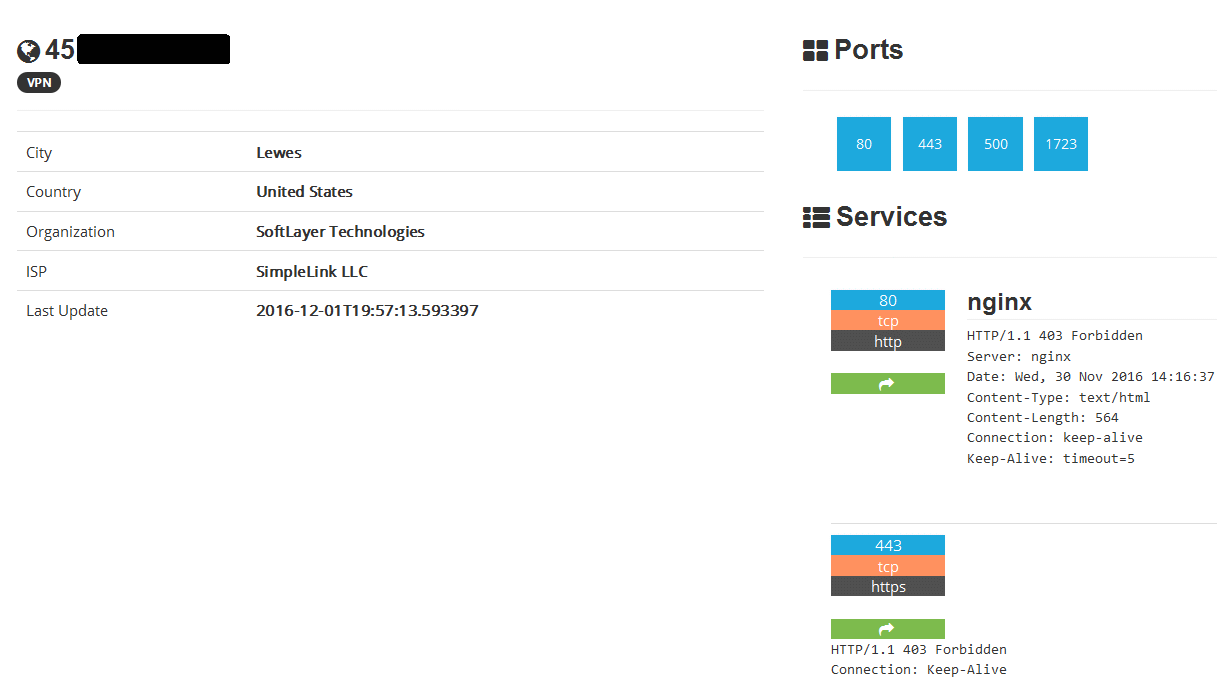

![Shodan Command Line a Step by Step Walkthrough - HackingPassion.com : root@HackingPassion.com-[~] Shodan Command Line a Step by Step Walkthrough - HackingPassion.com : root@HackingPassion.com-[~]](https://hackingpassion.com/wp-content/uploads/2020/03/shodan-vulns.png)


